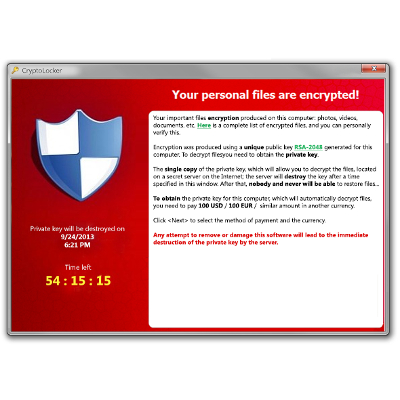
In September, a new kind ransomware burst onto the It security scene and it has been wreaking havoc on computer networks all over the world ever since. The virus has been named CryptoLocker, it’s capable of completely taking over your system, encrypting your files, and holds your data ransom until you pay them the money they demand. If you don’t pay, then your files are deleted. Here’s what you need to know.
How CryptoLocker Works
One thing that you never want to do is pay the ransom, which is currently $300. Most organizations will even identify their data as the company’s most valuable asset because conducting business without access is not possible. The hackers fully expect that a company infected with CryptoLocker will loose access to their data, panic, and pay up thinking its cheaper to pay the hacker then to lose valuable production time. CryptoLocker is using fear as a weapon because a clock counting backwards from 100 hours is included with the alert that your computer is being help hostage. If the clock strikes 0:00, and the ransome hasn’t been paid, then your data will be deleted. If your business isn’t prepared for security breaches like CryptoLocker, then you will be looking at a stressful 100 hours to come up with a solution.
Can You Stop CryptoLocker?
You may think that if you get infected you can just reboot your PC or run a a security scan in safe mode. Not so fast. CryptoLocker is designed to prevent common troubleshooting procedures. In fact, with every computer restart CryptoLocker will make changes to your registry further embedding itself into your system., and don’t even think about accessing your drive remotely, because upon infection, one of the first actions taken by the virus is to encrypt the files on both your local and remote drives.
Without a reliable and properly tested data backup solution in place, the only available option you have that will recover your files is to follow the hacker’s instructions and send money to their untraceable account. Just because you have paid the ransome doesn’t always mean you are in the clear. Paying the ransom will only give you access to your individual PC, and there are several reports of users that have paid but they were still not restored full access to the machine. Meanwhile, the virus is still on your system running in the background, waiting to infect other machines on your network.
CryptoLocker is Spreading Fast
Despite every major technology company alerting their customers about CryptoLocker (Quikteks informed our clients on our blog about it last September), the virus continues to spread and catches users and organizations worldwide in in its clutches. There was even a case reported in November where a police department in Massachusetts paid the hackers $750 worth of Bitcoins to get the private encryption key that would restore access to their files.
To help give you perspective on how fast CryptoLocker is spreading, spam filter AppRiver quarantined 56.6 million emails in October that contained a virus in the attachment, and they reported that CryptoLocker was by far the most common malware. Other IT Security companies are also reporting that they’re seeing thousands of new CryptoLocker infections every day.
There are several ways that the CryptoLocker virus spreads, but the most common way is via email. Using a hacking strategy called social engineering, the hacker sends an email to your inbox that will look like a credible message from a trusted source. A fake message about an expected delivery from a parcel service is the most common example. An email like this will ask you to download the infected attachment by saying that it contains important information about your order or delivery.
The CryptoLocker attachment is a .ZIP file in most cases, which means that it will pass through through standard filtering. A user may look at the attachment and think that it looks safe to download because it looks like a .PDF or .DOC file, but it’s really a double extension that hides the true .EXE. As soon as you click the attachment, the virus is executed and encryption of your data begins. Other ways that CryptoLocker spreads includes online social media games and clicking on malware pop-up advertisements on websites.
3 Actions You Can Take to Prevent CryptoLocker Infection
- Be Wary of Suspect Emails and Don’t Visit Disreputable Websites: Don’t open suspicious emails or visit websites of low reputation, and never download a file unless you’ve scanned it and you’re absolutely sure of what it is. Also, do not respond to unsolicited emails from unknown sources or download unfamiliar social media games, and vnevert disable your antivirus software for any reason. Some malware will actually request this.
- Have and Up to Date Security Solution: You will want to make sure that you’re running updated antivirus and antimalware software as well as have a strong firewall in place. A Unified Threat Management tool from Quikteks is the strongest network security solution offered on the market today, and it includes content filtering to block employees from visiting websites that reduce productivity and create problems.
- Implement a Data Backup and Recovery Tool: One of the most important things you can do to protect your data from CryptoLocker is to back up your data and have several ways to recover it. A Backup and Disaster Recovery (BDR) tool from Quikteks is great for this because it takes several snapshots of your data throughout the day and then backs everything up both locally and in the cloud. This means, if your company gets infected with CryptoLocker (and it shouldn’t if you followed steps 1 and 2), then we can to a restore to a previous version of your data that doesn’t contain the ransomware.
CryptoLocker is one of the worst viruses ever to hit the web and it plays on people’s fears, but with Quikteks watching over your network infrastructure with our managed IT services, you don’t have to be fearful of even the worst types viruses on the Internet. To learn more about CryptoLocker, or to receive a free network audit and security assessment where we scan your system to discover if malware like CryptoLocker is lying dormant in your system, give us a call at PHONENUMBER.